Case Study – BFSI DevOps Implementation And Optimization
About Client
A BFSI company, housing a large portfolio of applications with a majority of them outsourced to external vendors was facing significant challenges in its software development and maintenance processes. Among these applications, 15 were identified as core applications critical to the company’s operations. The existing technology stack relies on a proprietary database, and certain applications incorporated forms as part of their architecture.
The Future State Aspirations
The company aspires to set up a matured DevSecOps environment and achieve – Near-zero touch pipeline for all product development for infrastructure provisioning, application build and deployments, and changes to configurations – Matured source-code management processes, including review gates, to ensure quality – Defined and repeatable release process including quality and security gates to achieve minimum deployment failures and bug leakage – Modernization to enable the utilization of the latest technological advancement – Common process among different vendors so that the BFSI company has a better understanding and control over the entry SDLC.
Challenges
- Lack of Source Code Management
- Absence of Documentation
- Lack of Common Processes
- Missing CI/CD and Automated Testing
- No Branching and Merging Strategy
- Inconsistent Sprint Execution:
Proposed Solution
These challenges collectively impede the company’s ability to achieve optimal software development, maintenance, and deployment processes. The absence of foundational practices such as source code management, documentation, and standardized processes hinders the company’s capacity to respond swiftly to market demands, implement changes efficiently, and maintain the overall health of its application portfolio. Addressing these issues is imperative for the BFSI company to attain a mature and efficient DevSecOps environment, ensuring the sustained success of its software development initiatives. After the initial analysis of the environment and getting a better understanding, we propose the scope of implementation in 2 stages.
Stage – 1 – Implement Basic DevOps( Source code, CI/CD process, etc.) in an iterative mode of 5-10 applications in one go, with the number of applications to be increased as the momentum increases.
Stage – 2 – Modernization (Microservices, Test automation, security, monitoring, etc.)
Injecting security in the SDLC
As security is a vast area, DevOps Enabler puts the security requirements separately. Injecting security into the SDLC has multiple facets and primarily includes:
- Security Requirements
- Security by Design § Secure Coding
- Static Application Security Testing (SAST)
- Dynamic Application Security Testing (DAST)
- Software Component Analysis
- Security Operations (including security monitoring for infra, network, and ops)
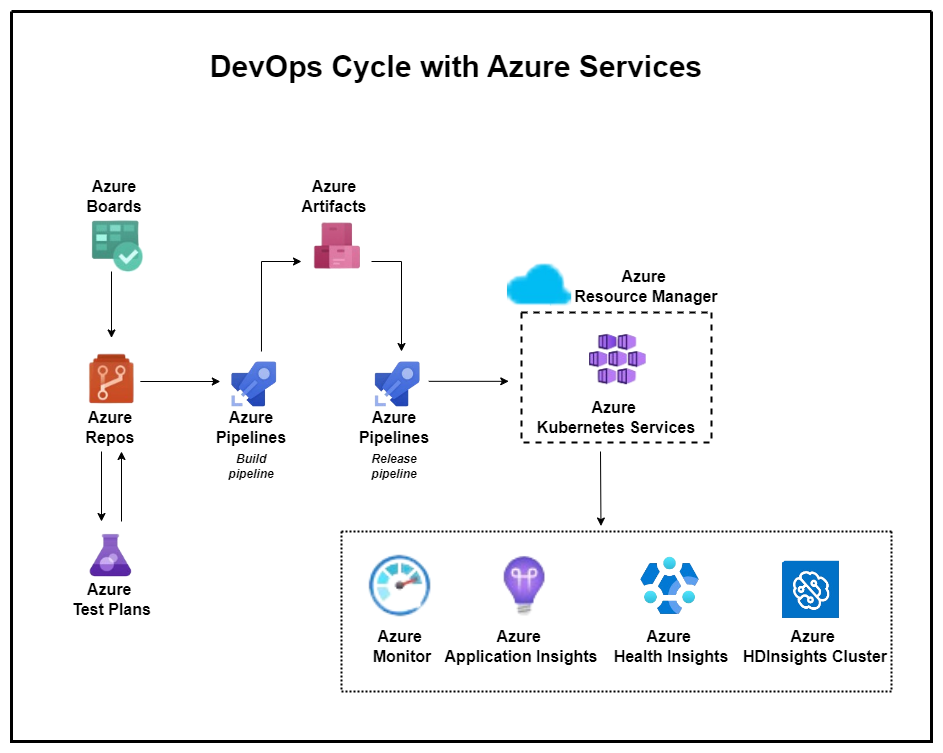
Outcomes
The proposed solution successfully addresses the challenges, aligns with future aspirations, and provides a phased implementation leveraging Microsoft Azure’s DevOps capabilities. This approach ensured a gradual and structured transformation towards a matured DevSecOps environment, enhancing collaboration, automation, and overall development efficiency within the BFSI company.
• Common Process Template, increasing the Sprint Visibility at different levels and across different vendors providing services.
• Azure DevOps Repos setup and migration ensures organized version control.
• Integration of Azure Boards and Pipelines enforces Sprint planning, backlog management, and streamlined development workflows.
• Azure Pipelines implementation achieves automated builds and deployments.
• Azure Repos strategies establish stability, and team education on best practices ensures effective branching and merging.
• Azure DevOps Wiki adoption facilitates documentation, knowledge sharing, and linkage with code repositories.
• Implementation of Azure DevOps Security features enhances security throughout the SDLC.
• Automation through Azure Automation and Infrastructure as Code (IaC) using ARM templates achieves efficient infrastructure provisioning and deployment.
• Integration with code quality tools, review gates, and pull request policies in Azure DevOps Repos ensures matured source code management.
• Azure Release Management implementation with security and quality gates achieves a defined and repeatable release process.
• Transitioned towards microservices architecture using Azure Kubernetes Service and end-to-end monitoring.
• Integration of Azure Test Plans for automated testing and Azure tools for security testing.
• Utilization of Azure Monitor, Security Center, and Sentinel for infrastructure and network monitoring, as well as security incident response.
Metrics
| Metric Categories | Lack of Source Code Management | No Documentation Available |
No Common Processes |
No CI/CD or Automated Testing |
No Branching and Merging |
Sprints not Followed |
|---|---|---|---|---|---|---|
| Stage 1 - Implement Basic DevOps | Repos & Git Implementation | Wiki Adoption |
Standardized Processes |
Pipelines & Testing |
Repos Strategies |
Boards & Pipelines |
| Metric Categories | Near Zero Touch Pipeline |
Matured Source Code Management |
Defined and Repeatable Release Process |
Modernization |
|---|---|---|---|---|
| Stage 2 - Modernization | Automation And IaC |
Code Quality & Review Gates |
Release Management with Gates |
Modern Technologies & AKS |
| Area | Achievement |
|---|---|
| Deployment Frequency | Multiple Deployments per Day / On-Demand |
| Code Review Effectiveness | 100% Review Completion |
| Testing Coverage | 80% to 90% Coverage of Codebase |
| Security Vulnerabilities | Zero Critical Vulnerabilities, Timely Remediation |
| Release Success Rate | > 95% Successful Releases |
| Infrastructure Provisioning | Automated Provisioning, < 15 Minutes |
| Project Completion Status | On-Time and Within Budget |
| Estimation Metrics | < 10% Variance Between Estimated and Actual |
| Schedule Adherence | > 95% Adherence to Project Schedule |
| Code Quality | < 90% |
| Defect Re-open Rate | > 5% Defects Re-opened After Closure |
| Work Items and Tasks | > 90% Completion Rate |
| Pull Requests | < 10% Rejected Pull Requests |
| Build and Release Pipelines | < 5% Failures |
| Sprint Completion Rate | > 95% Sprint Completion Rate |
